E-Mail-Verschlüsselung in der Praxis
Hintergründe zur Verschlüsselung
Für den sicheren Austausch von Daten zwischen einem E-Mail-Client und einem E-Mail-Server werden heute meistens verschlüsselte Kanäle benutzt. Dies wird z.B. durch das Verschlüsselungsprotokoll Transport Layer Security (TLS) ermöglicht, das auch bei HTTPS-Verbindungen zum Einsatz kommt. Anfangs- und Endpunkt des Datenflusses sind dabei meistens über mehrere Server oder Punkte miteinander verbunden. An diesen Punkten liegen die Daten unverschlüsselt vor, bevor sie für das nächste Teilstück der Strecke wieder durch einen verschlüsselten Kanal geschickt werden. Deshalb wird hier auch von Punkt-zu-Punkt-Verschlüsselung gesprochen.
Im Unterschied dazu werden bei Ende-zu-Ende-Verschlüsselung (E2E) statt der Verbindung die Daten selbst (in unserem Fall die E-Mails) verschlüsselt, bevor sie von der Senderin oder dem Sender auf die Reise durch das Internet zur Empfängerin oder dem Empfänger geschickt werden. Erst beim Ende ihrer Reise können sie von der Empfängerin oder dem Empfänger wieder entschlüsselt werden und sind auf dem gesamten Weg dazwischen ohne Unterbrechung geschützt.
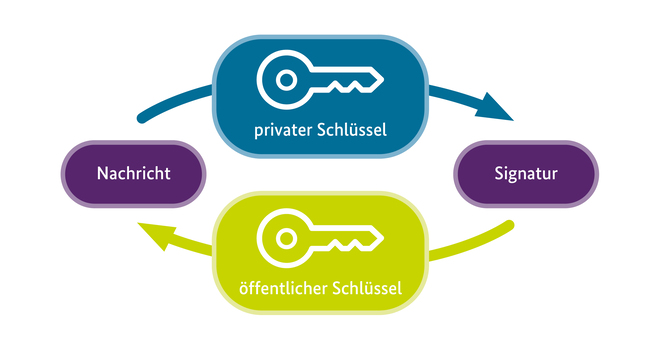
Um eine E-Mail Ende-zu-Ende zu verschlüsseln, wird die sogenannte asymmetrische Verschlüsselung benutzt. Senderin bzw. Sender und Empfängerin bzw. Empfänger erzeugen dazu jeweils ein Schlüsselpaar. Dies besteht aus einem privaten bzw. geheimen Schlüssel, den sie behalten und nicht weitergeben, und einem öffentlichen Schlüssel, den sie verteilen. Mit dem eigenen privaten Schlüssel können empfangene verschlüsselte E-Mails entschlüsselt und versendete E-Mails kryptografisch signiert werden. Mit dem öffentlichen Schlüssel kann jeder E-Mails an die Besitzerin oder den Besitzer des öffentlichen Schlüssels verschlüsseln und die Signatur von E-Mails, die diese(r) verschickt, prüfen. Das gleiche gilt umgekehrt für alle Kommunikationspartner und ihr Schlüsselpaar.
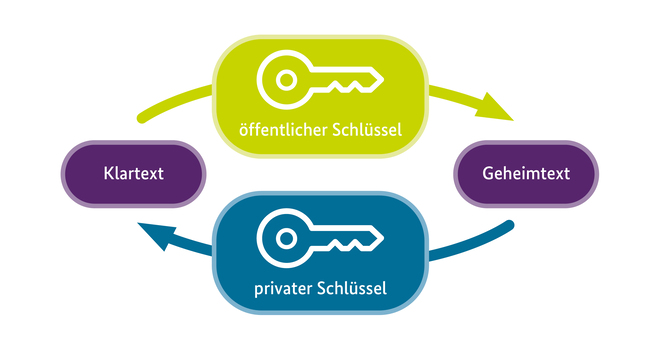

Auf diese Weise kann durch die Verschlüsselung der E-Mail die Vertraulichkeit und mit der Signatur ihre Integrität (die E-Mail wurde zwischen Absenden und Empfangen nicht geändert) und Authentizität (sie stammt wirklich von der Besitzerin bzw. dem Besitzer des privaten Schlüssels) gewährleistet werden. Natürlich müssen vorher noch die öffentlichen Schlüssel ausgetauscht werden, was dadurch stark vereinfacht wird, dass der öffentliche Schlüssel eben nicht geheim ist und von jedem abgerufen werden kann.

Für den Austausch gibt es verschiedene Möglichkeiten, die weiter unten beschrieben werden. Bei jeder sollte überprüft werden, ob der Schlüssel wirklich der Kommunikationspartnerin bzw. dem Kommunikationspartner gehört und kein falscher Schlüssel untergeschoben wurde. Das kann je nach genutztem Tool automatisch unterstützt oder händisch selbst gemacht werden.
Trotz der vorhandenen Möglichkeit wird die Ende-zu-Ende-Verschlüsselung bisher nur sehr selten eingesetzt. Das ist unter anderem darauf zurückzuführen, dass die meisten Hersteller weit verbreiteter E-Mail-Programme diese Verschlüsselungstechnik nicht anbieten. Anwenderinnen und Anwender müssen sich dann selbst darum bemühen, ihr E-Mail-Programm mit entsprechenden Plugins zu erweitern. Dies müssen sowohl Senderin bzw. Sender als auch Empfängerin bzw. Empfänger machen, damit die E2E-Verschlüsselung funktioniert. Auch wenn bei der Installation und Konfiguration in den letzten Jahren die Nutzerfreundlichkeit durch weitgehende Automatisierung stark verbessert wurde, ist die Anwendung ohne Hintergrundkenntnisse nach wie vor wegen unterschiedlicher Schlüsselverteilungsprozesse nicht einfach. Deswegen werden im Folgenden ein paar Informationen und Hinweise gegeben, die dabei helfen können, E2E erfolgreich einzusetzen.
Die richtige Geheimsprache wählen
Damit Senderin bzw. Sender und Empfängerin bzw. Empfänger verschlüsselt miteinander kommunizieren können, müssen sie sich auf die gleiche Geheimsprache einigen. Das heißt, dass die E-Mail-Programme von beiden die gleichen Protokolle unterstützen. Schon seit vielen Jahren haben sich dafür die zwei Protokolle bzw. Standards S/MIME und OpenPGP etabliert. Zwar benutzen beide die gleichen Algorithmen und Mechanismen für die Kryptografie, sie unterscheiden sich aber in dem Vertrauensmodell der Schlüssel und ihrer Verwaltung, so dass sie nicht kompatibel miteinander sind. Je nach Einsatzszenario haben beide Protokolle Vor- und Nachteile.
Für den Austausch von E-Mails im Umfeld von Behörden und Firmen wird meistens das Protokoll S/MIME benutzt, im privaten Umfeld OpenPGP. Einige E-Mail-Programme benötigen zur Verschlüsselung ein entsprechendes Plugin, das nach Auswahl des Protokolls installiert und konfiguriert werden muss.
S/MIME
Das S/MIME (Secure/Multipurpose Internet Mail Extensions) Protokoll nutzt eine hierarchische Public Key Infrastructure (PKI). Im Zusammenhang mit S/MIME wird meistens von Zertifikaten statt Schlüsseln gesprochen. Den Vertrauensanker bildet dabei die Root Certificate Authority (Root CA), die das Root Certificate sicher verwahrt. Mit diesem sind Zertifikate der untergeordneten Certificate Autorities (CA) beglaubigt. Diese wiederum stellen die Zertifikate für die Endnutzerinnen und -nutzer aus und beglaubigen diese. Die Gültigkeit und Authentizität eines Endnutzerzertifikates kann durch das Prüfen der Zertifikatskette bis zum Root Certificate verifiziert werden.
Die benötigten Schlüsselpaare bzw. Zertifikate werden dabei üblicherweise nicht von den Nutzerinnen und Nutzern selbst erzeugt und verteilt, sondern von Organisationen oder Firmen, und sind zumeist kostenpflichtig. Daher eignet sich S/MIME vor allem für Unternehmen oder Behörden und weniger für den privaten Gebrauch. Im Folgenden wird S/MIME deswegen nicht weiter betrachtet.
OpenPGP
Bei OpenPGP ist das Vertrauensmodell für die Schlüssel viel flacher organisiert, oft auch in einem sogenannten Netz des Vertrauens (Web of Trust), bei dem indirekt einem fremden Schlüssel vertraut wird, der von jemandem signiert wurde, dem vertraut wird. Die Schlüssel werden von Nutzerinnen und Nutzern selbst erstellt und verwaltet.
Bei der Bewertung des Vertrauens in die Schlüssel der Kommunikationspartner helfen einige E-Mail-Tools. Dabei hängt das Vertrauen oft von der Quelle oder dem Weg ab, über den der Schlüssel bezogen wurde. Zum Beispiel kann ein Schlüssel per E-Mail, Schlüsselserver (der die Authentizität prüft oder auch nicht), Webseite oder auch persönlich auf einem USB-Stick erhalten werden. In jedem Fall kann die Authentizität des Schlüssels überprüft werden, indem der eindeutige Fingerabdruck des Schlüssels über einen anderen Kanal abgeglichen wird (z. B. Telefon oder Messenger) als der, über den der Schlüssel erhalten wurde.
E-Mail-Tools
Im Gegensatz zu Messengern, bei denen Nachrichten nicht zwischen unterschiedlichen Apps wie z. B. Signal und WhatsApp ausgetauscht werden können, können E-Mails kompatibel zwischen verschiedenen Anwendungen und auch betriebssystemübergreifend ausgetauscht werden.
Hier sind ein paar Beispiele für E-Mail-Tools, die E2E mit OpenPGP unterstützen, auf den gängigen Plattformen aufgelistet:
Linux:
- Thunderbird (direkte Unterstützung)
- Kmail (grafische Zertifikatsverwaltung mit Kleopatra)
Android:
- FairEmail (mit Plugin OpenKeyChain)
- K9 Mail (mit Plugin OpenKeyChain)
MacOS:
- Thunderbird (direkte Unterstützung)
Apple Mail (mit Plugin GPGTools / GPG Suite)
Windows:
- Thunderbird (direkte Unterstützung)
Outlook (mit Plugin Gpg4win)

Schlüssel austauschen und verifizieren
Der Vorteil bei asymmetrischen Verschlüsselungsverfahren ist, dass der öffentliche Schlüssel auch über unsichere Wege ausgetauscht werden kann, da er nicht geheim ist. Wie oben erwähnt, kann ein öffentlicher Schlüssel auf verschiedenen Wegen ausgetauscht werden, z. B. von einem Key-Server, angehängt an eine E-Mail oder über WKD/WKS (s.u.) vom E-Mail-Provider. Allerdings sollte vor seiner Nutzung sichergestellt werden, dass der Schlüssel wirklich zu der Adresse gehört, die angegeben wird. Je unsicherer die Quelle ist, von der der Schlüssel bezogen wurde, desto gründlicher sollte er verifiziert werden. Der private Schlüssel hingegen darf nicht verloren gehen oder in fremde Hände geraten.
Schlüsselaustausch über Key-Server
Wenn der öffentliche Schlüssel von seiner Besitzerin oder seinem Besitzer auf einen Key-Server hochgeladen wird, wird von diesem Server die Zuordnung zur E-Mail-Adresse nicht unbedingt geprüft. Deswegen können auch andere Personen diesen öffentlichen Schlüssel zum Key-Server hochladen, obwohl sie nicht die Besitzer sind, was nicht weiter stört, da der Schlüssel ohnehin veröffentlicht werden soll.
Es kann jedoch passieren, dass jemand einen selbst erzeugten öffentlichen Schlüssel mit einer fremden E-Mail-Adresse verknüpft und zum Key-Server hochlädt. Wenn Kommunikationspartner dann den öffentlichen Schlüssel eines Adressaten anhand dessen E-Mail-Adresse auf dem Key-Server suchen, werden so mehrere passende Schlüssel auf dem Key-Server gefunden. Dann ist es für den Nutzenden nicht ohne Weiteres möglich, den richtigen herauszufinden. Wird der falsche Schlüssel benutzt, so kann der oder die berechtigte Empfänger(in) die E-Mail nicht entschlüsseln, dafür aber derjenige, der den falschen Schlüssel hochgeladen hat. Inzwischen gibt es jedoch immer mehr Key-Server, die überprüfen, dass ein hochgeladener Schlüssel zu der richtigen E-Mail-Adresse gehört.
Schlüsselaustausch per E-Mail
Als weitere Möglichkeit kann der öffentliche Schlüssel der Kommunikationspartnerin oder dem -partner offen per E-Mail übersandt werden. Auch bei diesem Verfahren ist die Authentizität des öffentlichen Schlüssels nicht sichergestellt. Durch zum Beispiel eine "Man-in-the-Middle-Attacke" könnte ein Angreifer diese E-Mail abfangen und den Schlüssel durch seinen eigenen öffentlichen Schlüssel ersetzen. Der Kommunikationspartner verschlüsselt seine Nachricht dann unwissentlich mit dem öffentlichen Schlüssel des Angreifers, der diese Nachricht dann mit seinem privaten Schlüssel lesen kann. Eine korrekte Assoziierung des Schlüssels mit der passenden E-Mail-Adresse ist also nicht zwingend gegeben.
Automatisierter und verifizierter Schlüsseltausch mit WKD/WKS
Mit dem Protokoll Web Key Directory (WKD) und Web Key Service (WKS) werden öffentliche Schlüssel ganz automatisch verteilt, ohne dass die Nutzerinnen und Nutzer dies bemerken. Voraussetzung dafür ist, dass das E-Mail-Tool und die beteiligten E-Mail-Provider die Protokolle unterstützen. Dann wird der eigene öffentliche Schlüssel automatisch nach Erzeugung zum Provider hochgeladen und nach Überprüfung der E-Mail-Adresse veröffentlicht. Wird bei Erstellung einer neuen E-Mail die Adresse der Empfängerin oder des Empfängers angegeben, nimmt das Tool im Hintergrund automatisch Kontakt mit deren oder dessen Provider auf und lädt den passenden Schlüssel herunter, so dass er sofort für die Verschlüsselung genutzt werden kann. Das ist insofern konsequent, da dem E-Mail-Provider ohnehin ein gewisses Vertrauen entgegengebracht wird, wenn die E-Mails über dessen Server ausgetauscht und dort gespeichert werden. Allerdings unterstützen bisher nur wenige Provider wie Posteo WKD und WKS.
Das Austauschverfahren mit WKD/WKS wurde im Auftrag des BSI in dem Projekt EasyGPG entwickelt.
Unabhängig vom Verfahren, wie die Schlüssel ausgetauscht wurden, können versierte Nutzerinnen und Nutzer die Authentizität der Schlüssel selbst händisch überprüfen. Dazu wird nach dem Austausch der Schlüssel über einen anderen Kommunikationskanal (z. B. Telefonanruf) die eindeutige Prüfsumme (Hashwert) eines Schlüssels abgeglichen. Die Prüfsumme kann in der Schlüsselverwaltung von den E-Mail-Tools angezeigt werden. Dies bedeutet jedoch zusätzlichen Aufwand und die Bereitschaft, sich auch auf technischer Ebene stärker damit auseinanderzusetzen.
- Kurz-URL:
- https://www.bsi.bund.de/dok/11486410


