Software Updates - A Pillar of IT Security
Why should you install updates regularly and as soon as possible after release?
Updates, Patches, Bugfixes - what exactly do all these terms mean?? In fact, they all refer to the same thing: The manufacturer correcting errors, eliminating vulnerabilities or adding functions without the user needing to reinstall the software. Vulnerabilities are security-related weaknesses in a piece of software that allow criminals to attack systems, perhaps by installing malware or taking over control of devices belonging to others.
Putting off installing updates? Do not delay! Download our Five tips graphics package to find out why you should always update your system as soon as possible when an update is released.
Major software development houses for information technology provide regular monthly updates on 'patch days' so that you can enhance and 'immunise' your systems. This is a huge advantage for consumers: if you regularly update your smartphones and computers, they will have protection against new threats from the Internet and from the installation of malware. The device is able to defend itself against the risk before any damage can be inflicted. This is why patches are one of the most effective ways to prevent attacks from the internet.
Any system - whether it's an operating system for PCs and laptops, an app on a smart TV, software on a smartphone or a virus protection program - can only provide effective protection against threats to your computer if it is up to date. In this video, BSI expert Manuel Bach explains the key facts about updates:
Maintain an overview
As users often have many different software products installed at the same time, it can be difficult to maintain an overview. Our guide explains how you can easily check your software update settings and keep all your systems up to date with as little effort as possible to protect yourself against any nasty surprises.
- Get an overview of the programs you use.
In addition to your operating system and browser, you may also use the Office package, media players or anti-virus software. It is important to know what programs you have installed not only on your desktop PC, but also on your laptop, tablet or smartphone. - Check which products have an automatic update service.
If you don't know which products regularly download automatic updates, take the time to check in the online help or your software settings. If you can't find out from these sources, try searching the internet for the application name with the words "automatic updates". - Get into the habit of reading messages about updates rather than minimising them.
We are confronted with so many unwanted pop-ups that clicking to get rid of them becomes the standard course of action - no matter what they contain. Get into the habit of quickly checking the content of a pop-up to make sure that it isn't an important warning or instruction before you close it. - Create an overview of the programs you have to manually check for updates.
If you find that there is no automatic update service for one or more of your main programs, it is a good idea to compile a list. - Check for updates regularly - keep an eye on the manufacturer's newsletter or specialist publications.
The BSI's Citizen CERT service publishes a newsletter that provides information on all the latest developments. - Install updates as soon as possible after they are released.
Cyber criminals know that an update is likely to be released very soon after a vulnerability is discovered. This is why they try to use those first few days to exploit the vulnerability by programming viruses and worms and releasing them for circulation. Make sure that you act faster than the criminals. - Don't be fooled by fake updates.
Unfortunately, the criminals who program computer viruses often exploit the desire of users to keep their systems up to date: they might send out fake warning e-mails and display confusing pop-ups on websites. As a rule, you should only install updates when you have been notified of them in the proper way by a trusted source. Look out for messages warning you that support for your product is about to end.
Software providers will often only provide updates for specific products for a certain period of time. One example is Microsoft's decision to end support for Windows 7. If a manufacturer stops offering software updates for a product, consider whether you can switch to an alternative product.
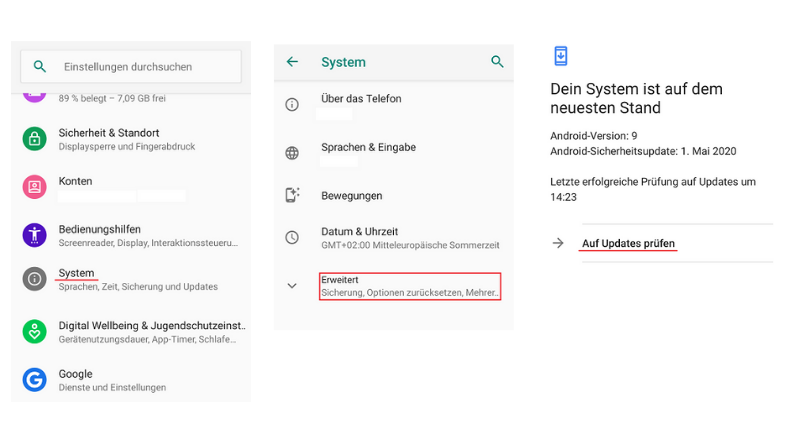
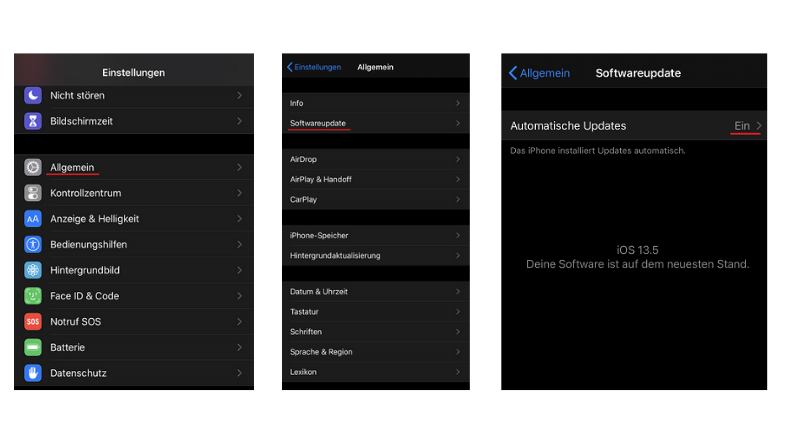
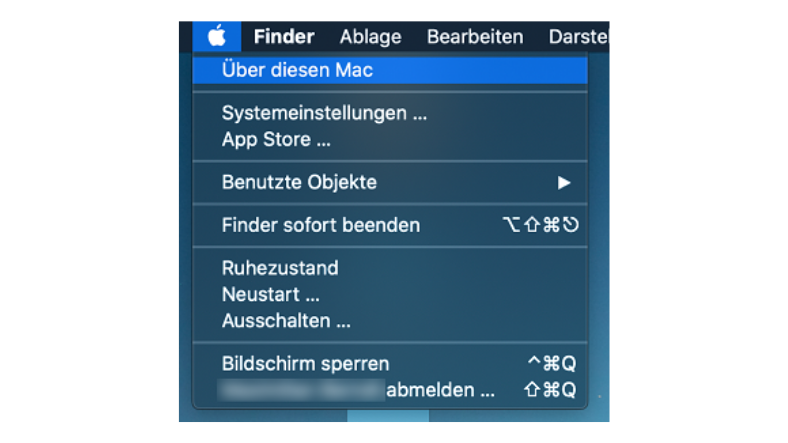
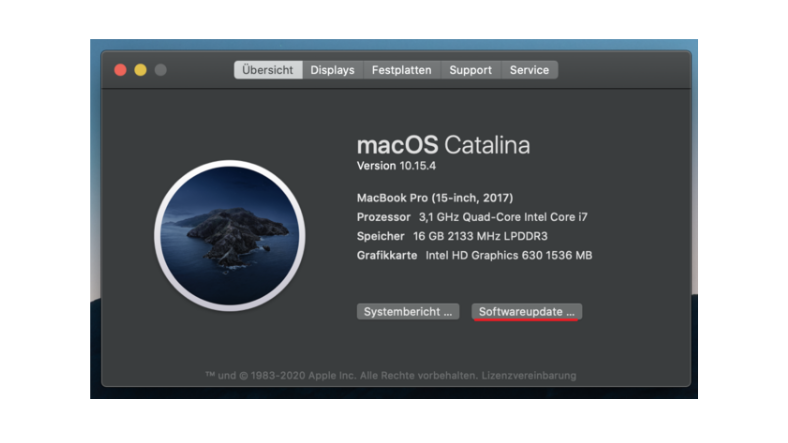
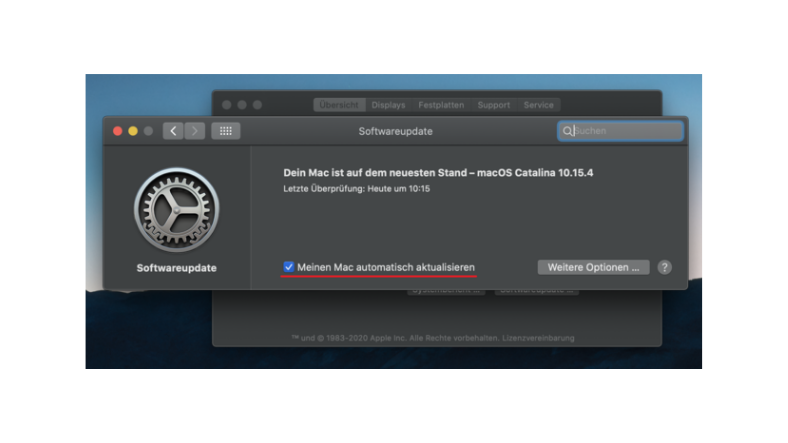
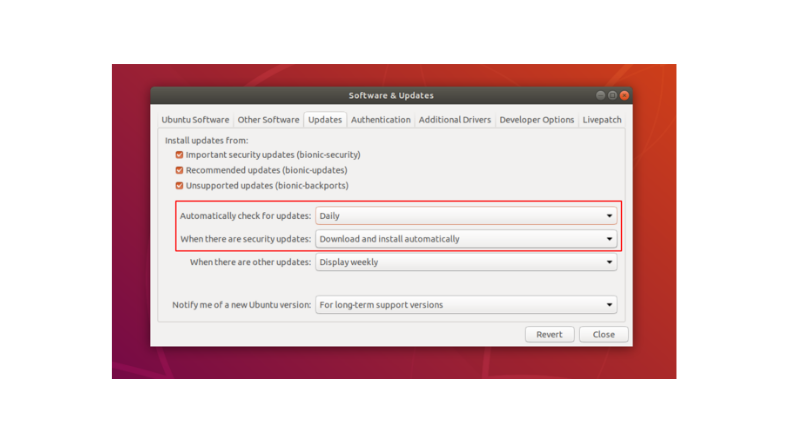
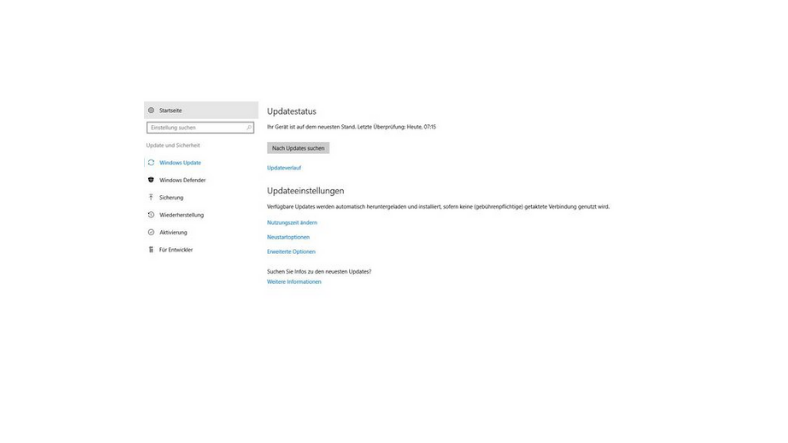
Are automatic updates activated on my device?
All software needs to be regularly updated to protect the device. This is true for everything from Office applications to e-mail programs and video games, as well as the operating systems on computers, smartphones and tablets. The major operating systems allow you to check whether automatic updates are activated or whether new updates are available.
Side note: The basics of IT security
In spite of all this evidence, statistics show that users underestimate the effectiveness of updates and rely instead on anti-virus programs and firewalls. The BSI has compiled a list of the most important, commonly used protective measures that can be used to safeguard PCs, smartphones and tablets.
(Automatic) updates
The programs and operating systems installed on all digital devices can only effectively protect themselves against viruses, trojans and other threats when they are fully up to date. Most systems have an automatic update feature. This means that the device lets you know when a new patch is available and installs it in the background.
Use different strong passwords
"One account, one password" is an important security rule. If you stick to it, a criminal who discovers one of your passwords won't be able to access all your other user accounts. However, if you only have a few passwords that you use for lots of accounts, all of your accounts will be affected if one password is breached. To make it harder for a potential attacker to guess your password, use strong passwords wherever possible. Password managers can help you to generate strong random passwords and manage them securely.
Two-factor authentication
Two-factor authentication ensures that your user account remains protected even if your password gets into the wrong hands. With two-factor authentication, a second factor is requested after the first factor, which is usually a password; this second factor could be your fingerprint or a TAN.
If you take these three tips on board and use an anti-virus program and firewall on your PC (the products integrated into your operating system are often adequate), your technology will have the important tools it needs to defend itself against threats. Download our brochure to find out what else you need to do to avoid threats and problems online. Detailed instructions on update settings are provided in our article on installing updates.
- Short URL:
- https://www.bsi.bund.de/dok/6599164