Active crime groups in Germany
Explanations and tabular overview
Status: 08.04.2025
Financially motivated attackers target the assets of those affected in a variety of ways. From fraud and theft to extortion, the BSI observes new attack campaigns on a daily basis. According to the BSI, ransomware and data leaks currently pose the greatest cybercriminal threat to the state, economy and society.
In recent years, the BSI as well as national and international partners have increasingly observed so-called Cybercrime-as-a-Service (CCaaS). This involves outsourcing elements of a cyberattack to specialised attacker groups, similar to outsourcing services. CCaaS allows an attacker to obtain almost every step of an attack as a service from other cybercriminals or at least the malware required for it. The selling of malware is referred to as Malware-as-a-Service (MaaS). MaaS specialising in ransomware are called Ransomware-as-a-Service (RaaS).
Attackers that sell access to networks are called access brokers and the service Access-as-a-Service (AaaS). Emotet and QakBot were two well-known malware families that were probably used by access brokers. Access brokers aim to gain long-term access to a network. To do this, they usually load additional malware via so-called loaders.
Where possible, cybercriminal attackers are categorised into groups based on the malware used and their approach. The following table highlights some attacker groups that the BSI believes pose an increased threat to German organisations. The BSI is also monitoring other attacker groups that are probably also active against German organisations.
| Groupname | Exceptional characteristics | Description |
|---|---|---|
Bitwise Spider - Activity decreased substantially - |
|
|
Brain Spider - Activity decreased substantially - |
| |
| Frozen Spider (aka White Kali) |
|
|
| Graceful Spider (aka ATK103, Chimborazo, DEV-0950, Dudear, FIN11, G0092, Gold Tahoe, Hive0065, Lace Tempest, SectorJ04, Spandex Tempest, TA505, White Austaras) |
|
|
| Honey Spider | ||
| Lunar Spider (aka Gold Swathmore, White Khione) |
| |
Ocular Spider (aka White Enbarr, Spoiled Scorpius) |
| |
| Punk Spider (aka White Lilith) |
| |
| Recess Spider (aka White Peryton) |
|
|
| Scattered Spider (aka 0ktapus, Dev0671, Dev0875, Dev0971, Muddled Libra, Octo Tempest, Oktapus, Roasted 0ktapus, Scatter Swine, Scattered Swine, StarFraud, Storm-0875, UNC3944, White Dev 146) |
|
|
Traveling Spider (aka Gold Mansard, White Imp) | ||
| Vice Spider (aka White Nefas, DEV-0832, Vanilla Tempest, Vice Society) |
| |
White Dev 115 - Activity decreased substantially - |
|
|
| White Fenrir |
|
|
| White Kore |
|
|
| White Veles (aka DEV-0504, Velvet Tempest) |
|
|
| White Yama |
|
|
Footnotes:
1 Restricted MaaSs are MaaSs that openly recruit new affiliates and, for example, require affiliates to go through an application process before they are granted access to the service.
2 Private MaaSs are MaaSs that do not openly recruit new affiliates. The service is available to a limited group of affiliates and new affiliates tend to be added by invitation.
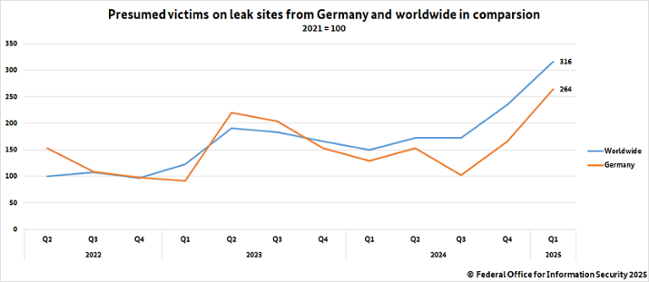
Leak victim statistics:
Since 2021, ransomware attacks have usually been accompanied by a data leak. The combined extortion with data encryption through ransomware and data publication through data leaks is known as double extortion. The BSI monitors so-called leak sites on which attackers publish the names and stolen data of victims of their ransomware attacks if they do not give in to cyber extortion.
These leak pages can therefore be used to record presumed victims who have been threatened with the publication of their data. In this respect, the leak victim statistics are not statistics on ransomware attacks, but on victims of hush money extortion. The BSI refers to "presumed" victims, as being named on a leak page under the control of an attacker does not necessarily mean that an attack actually took place. In some cases, attackers mention names for the sole purpose of blackmail without an actual attack having taken place.
The monitoring of leak pages only covers some of the ransomware victims. This means that, generally, only those organisations that refuse to pay a ransom or hush money are named and published on leak pages. Not all ransomware attackers use a leak page either. A large number of ransomware victims therefore remain unidentified. Consequently, this data collection does not provide any information on how many of the actual victims decide to pay a ransom or hush money. Moreover, the time of publication does not provide any information about exactly when the ransomware attack took place, which may have been a long time before. On top of that, the categorisation of presumed victims by country is only an approximation, as it is usually based on the location of the presumed victim's main office. This means that the attacked network segment may have been located in other parts of the world, especially in the case of globally active companies.
The indices in the diagram measure the naming of presumed victims on leak sites. The average for the year 2021 is used as the basis.