Top 10 Ransomware measures

Ransomware Killchain
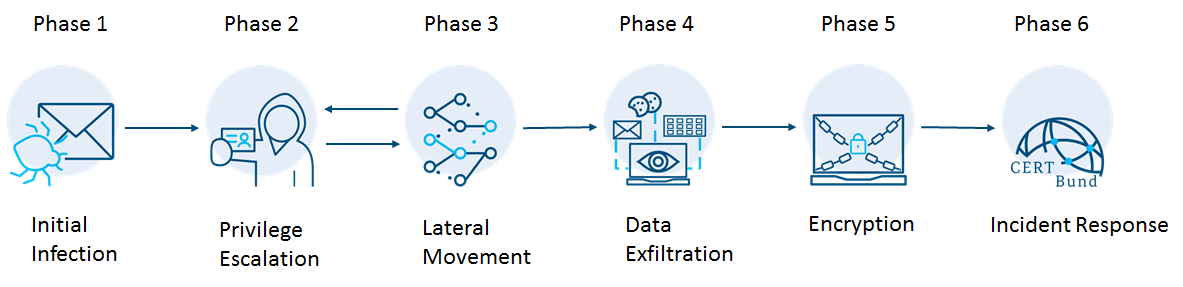

Measures against a ransomware attack
1. Patches and Updates
Exploiting a vulnerability in a software program (most of the time already fixed by the manufacturer) is one of the three most common vectors of entry for ransomware groups. attack vectors?
To protect against infections caused by exploitation of vulnerabilities that have already been fixed, updates should be applied to IT systems immediately after they are made available by the respective software manufacturer. Ideally, updates are distributed via a central distribution system. Updates that close highly critical vulnerabilities and/or relate to particularly exposed software (e.g. firewall products, web servers) should be prioritized.
Effect in Phase: 1
2. Remote Access
Attackers often try to install ransomware on systems via compromised remote accesses. Therefore, remote accesses should also be secured. As a general rule, these should only be used via VPNs in conjunction with two-factor authentication.
Effect in Phase: 1
3. Emails und macros
Email should be rendered as plain text only (often referred to as "text-only" or "plain text" as opposed to "HTML email"). Another security advantage of this representation is that web addresses can no longer be hidden in the text representation (in an HTML email, for example, a link labeled www.bsi.de External Link" could actually point to the address "www.malicioussoftwaredownload.de External Link"). If this is not possible, at least the execution of active content should be disabled when using HTML email so that malicious scripts can no longer be executed in the email. Employees should receive practical training on the risks involved in dealing with email as part of awareness-raising measures. This applies in particular to employees from corporate divisions that have to deal with a high volume of external email communication (e.g., staff recruitment).
The following setting should be configured on the client for handling MS Office document macros (consider MIME/HTML encoding):
- JS/VBS: prevent automatic execution on double click.Measures against an
- disable macros in client (via group policy)
- configure trusted locations for macros in AD
- use signed macros
Effect in Phase: 1
4. Execution of Software
The majority of ransomware infections could be prevented if the execution of unwanted software is forbidden. A whole range of measures exist for this purpose. The most important of these is so-called "application whitelisting". This allows only approved programs to be executed. The administration of such whitelists is very time-consuming, so that as a first step only "application directory whitelisting" could be activated instead.
At the very least, it should only be possible to execute programs (via group policy) from directories where the user has no write access to (execution directory whitelisting), which is an effective measure to protect against the initial infection.
5. Anti virus solutions
New versions of malware are rarely detected immediately via local Anti-Virus (AV) signatures. Most infections with new variants of ransomware are detected by the intrusion prevention (IPS) modules and cloud services of AV software. Therefore, antivirus software should take advantage of these modules.
Effect in Phase: 1
6. Administrator accounts
In principle, only administrator activities should be performed with privileged accounts. These accounts should not be used to read email or surf the Internet. Administrators must have normal user accounts for this purpose. This should be enforced technically. Privileged accounts should always be protected by two-factor authentication. Domain administration accounts should not be used for client administration.
Effect in Phase: 2
7. Network segmentation
Strong network segmentation helps limit the damage, as it allows the ransomware to reach only the systems in the immediate vicinity. In particular, the secure use of administrator accounts (see previous measure) is of key importance, as otherwise a central component of the security concept would be undermined.
Effect in Phase: 3
8. Data backup concept and centralised data storage
A backup is the most important preventive measure to ensure the availability of data in the event of a ransomware incident. The data must be saved in an offline backup. These backups are separated from the other systems in the network after the backup process and are therefore protected against attacks and encryption.
A backup always includes the planning and preparation for restarting processes and restoring the data. These plans should also be subjected to a practical test in order to recognise complications and challenges in the restoration of backuped data before an emergency occurs. Attention should also be paid to the possibility of restoring process availability in the event of data loss.
A centralised backup also requires users to store their data centrally. The advantage of network drives is that access rights can be assigned on a need-to-know basis. It is also possible to change these at a later date. For example, users can be denied write access to archived old project data. This means that the data can still be accessed, but encryption by a ransomware with user's rights would no longer be possible.
Effect in Phase: 5
9. Hardening of the Active Directory (AD)
After the initial compromise, the attackers often target the central authentication and authorisation service in order to access clients and servers within the domain with extended rights and distribute the ransomware centrally.
In order to make it more difficult to compromise the Active Directory, further (basic) measures should be implemented in addition to the points already mentioned. The IT-Grundschutz protection module APP2.2 Active Directory Domain Services also provides guidance here.
Effect in Phase: 3
10. Emergency planning
For the worst-case scenario (all systems in the network are encrypted and an extortion letter is present), contingency planning should exist and the processes for responding to and recovering business-critical systems should be practiced at regular intervals. In particular, business-critical systems have to be identified in advance and alternative communications (outside the compromised network) must be prepared. Important phone numbers and contacts should be kept offline (paper).
Effect in Phase: 6
- Short URL:
- https://www.bsi.bund.de/dok/ransomware-links

