Questions and answers for operators of critical infrastructures regarding the obligation to report according to the German IT Security Act

-
The obligation to report according to Section 8b (4) of the BSI Act applies to operators of critical infrastructures that were identified as critical infrastructures within the meaning of the BSI Act based on the threshold values determined in the BSI Kritis Regulation.
The entry into force of the "Act on the Implementation of the EU Directive on Measures to Ensure a High Common Level of Security of Network and Information Systems in the Union" (NIS Directive Implementation Act) on 30 June 2017 results in the following new regulations for operators of energy supply networks, public telecommunications networks and publicly accessible telecommunications services:
1. Operators of energy supply networks
The obligation to report IT disruptions to the Federal Office for Information Security (BSI) has previously only affected operators of energy supply networks whose facilities were designated as critical infrastructures under the BSI Kritis Regulation. The Act on the Implementation of the NIS Directive extends this reporting obligation to all energy supply network operators.
2. Operators of public telecommunications networks and providers of publicly accessible telecommunications services
The Act on the Implementation of the NIS Directive also extends the existing obligation to report pursuant to Section 109 (5) of the Telecommunications Act (TKG) in that impairments of telecommunications networks and services must be reported to both the Federal Network Agency and the BSI if they lead or could lead to significant security breaches.
For the notification to the BSI, the notification form of the Federal Network Agency can also be used in compliance with the implementation concept, which can be found on the Federal Network Agency website.
A PGP key is provided below as a text file for confidential transmission of the notification form to the BSI pursuant to Section 109 (5) of the TKG:
PublicKey
Creation date: 17/7/2017
ID key: 6977BB6EB4D9BD70
Fingerprint: C02C B80C 09A6 235F AA52 4A8B 6977 BB6E B4D9 BD70
Key ID and fingerprint of the PGP key can be checked for consistency after import into your own PGP key collection.Operators of critical infrastructures as defined by the BSI Kritis Regulation who operate a public telecommunications network or provide publicly accessible telecommunications services must register a contact with the BSI.
-
Wording of the law (from Section 8b (4) BSIG):
Operators of critical infrastructures shall report the following disruptions to the Federal Office immediately via the contact point:
- Disruptions regarding the availability, integrity, authenticity and confidentiality of their information technology systems, components or processes that have resulted in a failure of or significant impairment to the functionality of the critical infrastructure that they operate
- Significant disruptions to the availability, integrity, authenticity and confidentiality of their information technology systems, components or processes that may lead to a failure of or significant impairment to the functionality of the critical infrastructure that they operate […]
Figure 1 illustrates the various cases in which a report must be made.
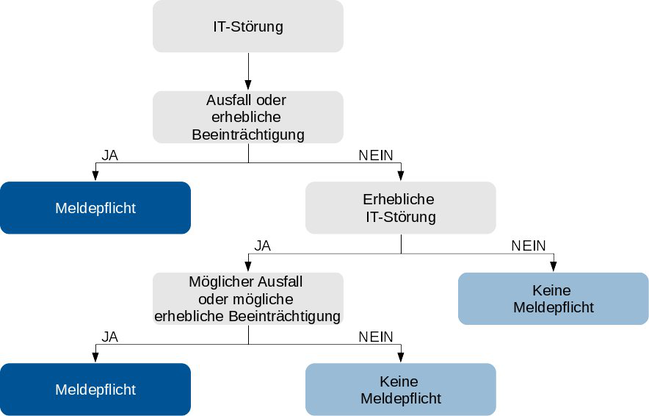
Abbildung 1: Meldekriterien für IT-Störungen Source: Bundesamt für Sicherheit in der Informationstechnik
If, despite all of these explanatory notes, identifying the IT disruption still remains difficult in a particular case, a more direct approach based on experience is simply to consider the following questions when deciding whether or not to report a disruption:
- Would it have helped me if I had received warnings about this type of incident from another operating company?
- Are the (potential) restrictions relevant for the supply situation?
In case of doubt, always contact the BSI. Our employees staffing the contact point will be happy to advise you about your reporting obligations.
-
To report a disruption to the BSI (see 'When must a report be made to the BSI?'), please always use the Reporting and Information Portal (MIP). In the password-protected area, you will find the menu item 'Reports', which you can use to make initial reports or provide further voluntary information about existing reports.
Encryption options for reports
We offer you the following alternatives for sending reports to the BSI over encrypted channels.
- S/MIME: the required certificate can be found at:
S/MIME certificate for reports - PGP: the public key can be found here:
PublicKey for reports
Fingerprint: CE98 82FB E72E E2CB F949 748C F01F 98FF 9268 0CFF
Key ID: F01F98FF 92680CFF
In order to be able to use S/MIME or PGP, you will need the corresponding programs/plug-ins, such as Gpg4win for the Windows operating system. After they have been installed successfully, you can then import and use the PGP key or the S/MIME certificate.
In the case of an S/MIME-encrypted response by the BSI, we will need your root certificate (root CA) for verification purposes.
You will find the root certificate (root CA) for the Federal Office PKI under Fingerprints and root certificate downloads.
- S/MIME: the required certificate can be found at:
-
The following explanation of an IT failure can be found in the explanatory statement to the German IT Security Act:
An [IT] failure as defined in the BSI Act therefore exists if the technology used is no longer able to fulfil its intended function correctly or in full, or an attempt has been made to cause this to happen. (cf. Bundestag printed paper 18/4096, 28)
Examples of IT failures that are not IT security incidents but must still be reported include:
- a digger that cuts through a cable
- a failure of the cooling system in a computer centre
- an incorrectly configured system
- an incorrect update or an incorrect patch that is loaded
-
Section 8b (4) No. 2 of the BSI Act states that an IT disruption must be significant to fulfil the reporting obligation. It is not possible to provide a clear answer that applies to every situation where a disruption is classed as significant. Instead of this, the persons in charge in KRITIS companies must make decisions on a case-by-case basis.
The following list of example criteria is only intended as a guide to provide a starting point. The example criteria take into account the IT side effects of the IT disruption, but not its influence on the critical service. This is only to be considered in a second step.
In particular, a significant IT disruption exists if
- a failure to deal with it would lead to increasingly negative effects (for example, if the failure of a control system would lead to increasingly extensive damage or the destruction of a system)
- additional efforts and resources are deployed or planned that go beyond the efforts and resources of regular operations or already planned work (for example, additional staff, overtime, deployment of replacement capacities, additional financial or material resources)
- the disruption must be dealt with by specially provided incident responders or incident teams
- important IT systems or components are shut down or isolated to avoid further effects
- operational processes are changed for the management period
- it causes significant financial damage
- there is a strong suspicion that the company is the target of a new, extraordinary, targeted or technically remarkable attack or attempted attack, for example an advanced persistent threat (APT)
- there are special reporting obligations to the company management for such IT incidents
Even if it was only determined afterwards that the IT disruption was significant in the sense of the BSI Act, it is reportable from that point on.
-
The incident must be reported immediately after the IT disruption was detected, i.e. without undue delay. All findings which are available at the time of the report must be reported to the BSI.
If it is not possible yet to provide all necessary information about the IT disruption as part of this immediate report, the report must be marked as an initial report. As soon as the missing information is known, a follow-up report and, finally, a final report must be submitted. When in doubt, reporting is subordinate to containing the acute consequences of the IT disruption.
As a matter of principle, the following applies to initial reports: speed must take priority over completeness.
A final report can be submitted after all measures to handle the incident have been implemented completely. With the final report, the operator has completely met their obligation to report for this IT disruption towards the BSI unless the BSI says something different to the operator within five working days (e.g. further questions regarding the incident).
-
A failure is when a critical infrastructure is no longer functioning. However, a scheduled interruption to operations is not considered a failure.
-
A significant impairment exists in particular when critical infrastructure is no longer able to provide its supply service as planned or expected, for example, because its functionality is only partially available and the resulting reduction in the service is significant. The question of when a reduction in a service is significant must be judged in proportion to the extent to which those being supplied are affected.
For example, a significant impairment can be assumed if:
- a large number of users are affected
- a large number of business processes are affected
- the impact draws public attention
-
Section 8b (4) Sent. 1 No. 2 of the BSI Act requires that a significant IT disruption could have led to a failure or impairment of the operated critical infrastructure -- if this is the case, the significant IT disruption would be reportable.
The following examples serve as orientation:
Significant IT disruptions occur during a planned business interruption that have a negative impact on the functionality of the critical infrastructure. Due to the planned service interruption, the planned supply capacity at this time is already 0 and will not be further reduced by the additional disruption.
For example: a patch is applied during a service interruption that disrupts the functionality of the system.
- Significant IT disturbances occur during a planned service interruption, which cause the service interruption to last longer than planned, but do not necessarily lead to a reduction in the supply service.
Significant IT disruptions occur that overcome several, but not all, of the protective mechanisms designed to protect against IT disruptions or limitations.
For example: An attacker gains access to the network of the critical infrastructure, but the supply service is not reduced as a result.
- Significant IT disruptions occur that lead to a failure or significant impairment of parts of a critical infrastructure, but do not actually reduce the supply service over their duration. This could be the case if part of the production or logistics chain within the critical infrastructure fails, but supply can be maintained at least temporarily through stockpiles.
- If attacks on the critical infrastructure are detected using novel, extraordinary, targeted or, from a technical point of view, remarkable attack methods, it must be assumed that an impact on the critical infrastructure is possible as soon as the attackers decide on this.
-
If you have not received an acknowledgement of your report by the BSI after 30 minutes at the latest, please additionally contact the BSI by phone. You can contact the BSI using the contact details made available to you after the registration.
-
If you have any questions when completing the reporting form, please contact the contact details made available to you after the registration.
If not all questions can be answered at the time of your report due to an ongoing IT failure, they must be supplemented afterwards in the follow-on report or final report.
Please make clear in the reporting form when you do no longer expect any additional information by marking it as a final report. With the final report at the latest, the information (section 3) about the probable or actual causes required for the statistics and the overall picture of the situation is to be provided.
-
The reporting form is subdivided into seven sections. The information which is provided by the party reporting in the first two sections is important for the following:
- establishing the contact (section 0)
- correlating the concernment (section 0, section 1)
- (statistical) follow-up (section 1)
In the following four sections, more precise details on the IT security incident are to be determined. This information is used for the following purposes:
- evaluating the criticality from an IT security perspective (sections 1-4)
- creating a nationwide picture of the IT situation (sections 1-4)
- warning or notification of potential other parties concerned (sections 1-4)
- (statistical) follow-up (sections 1-4, section 3 in particular)
- analysing the potential effects on the availability of critical infrastructures (section 1, section 5)
Moreover, you can provide supplementary information (section 6).
-
According to Section 8b (2) No. 2 BSIG [BSI Act], the BSI is obliged to "analyse potential effects on the availability of the critical infrastructures in collaboration with the competent regulatory authorities and the Federal Office of Civil Protection and Disaster Assistance (BBK)".
When required, the BSI approaches the competent regulatory authorities and/or the BBK. Where appropriate, the BSI forwards your report in an anonymised form (without section 0) to the competent regulatory authorities.
If you wish that your company is not mentioned to the regulatory authority, please make sure that NO INFORMATION about YOUR COMPANY enabling identification has been entered as text in the other sections.If you have stated in the reporting form where you have filed the complaint and mark that you explicitly wish that this information is forwarded accordingly, the BSI forwards this report, in addition to your collaboration with the local criminal prosecutors, to the Federal Criminal Police Office (BKA) as part of their legal competence for critical infrastructures. This means that the whole range of the police possibilities is available to you.
If facts indicating a terrorist background result from the report, the BKA must be informed by the BSI as part of their legal competence by the BSI.
If facts indicating a terrorist background result from the report, the Federal Office for the Protection of the Constitution (BfV) must be informed by the BSI as part of their legal competence by the BSI.
In individual cases, the BSI must inform their functional supervision in the German Federal Ministry of the Interior (BMI) about an IT security incident and the related technical aspects. The BSI will take measures which adequately protect the information transmitted in order to safeguard interests of the party concerned.
For the concrete processing of the case, the BSI approaches further authorities only in consultation with you.
-
The BSI analyses the IT failure, correlates it with other available findings and, where applicable, drafts proposals for measures. If additional details are required, the BSI contacts the contact person mentioned in the reporting form for the incident or, alternatively, the designated contact point of the operator in order to clarify any queries.
If the report and the information therein is relevant to other parties concerned, the BSI creates a warning or notification. Moreover, the findings are continuously included in the creation of an overall picture of the situation.
As part of the evaluation, the BSI also analyses the potential effects of the IT failure on the availability of critical infrastructures together with the BBK and the regulatory authorities.
-
The BSI treats your failure reports confidentially. Section 8d BSIG significantly restricts the disclosure of information to third parties. Information may only be provided if the interests worthy of protection of the concerned operator of critical infrastructures are not opposed to this and no impairment of the essential security interests is to be expected, because this information has been provided. Access to personal data shall not be granted.
If the BSI has created an anonymised information because of your failure report, they will not mention the name of the operator. The same applies if information that your company is concerned becomes known to the public via other routes during processing.
-
The visibility of IT attacks, as it is pursued by the reporting office of the BSI, should also be found again in criminal prosecution and the crime statistics. On the websites of the BKA, "Handlungsempfehlungen für die Wirtschaft in Fällen von Cybercrime" [Recommended actions for the economy in cases of cybercrime] can be found as an aid.
In the event of attacks and damage in your company, please check therefore actively whether it is possible to file a complaint.
-
Based on the BSI's constant gathering of information or the reports of the parties concerned, the BSI prepares sanitised warnings or notifications which are sent to registered operators on a target group basis.
In addition to this, the BSI provides all operators subject to reporting and, where applicable, also third parties with an overall picture of the situation.
A range of other products and services is being prepared.
-
The BSI understands the wording "available at all times" in the sense of Section 8b (3) of the BSI Act, to mean that operators are able to receive BSI products for warning and informing KRITIS-operators, hereinafter referred to as BSI products, (cyber security warnings, situation information etc.) via the registered contact point around the clock (24/7) and to view and evaluate them without delay (processing of information on demand).
As a rule BSI products are sent during normal business hours. However, the BSI's option to urgent warnings outside normal business hours (on public holidays, weekends or at night) cannot be ruled out in exceptional cases.
The BSI designs the cyber security warnings in such a way that urgency and (potential) need for action can be read (automatically) from the e-mail subject line. This enables permanently accessible services in an organisation, e.g. the gatekeeper, plant security or other on-call services, to recognise an acute need for action and, if necessary, issue an alert or forward it to suitable contacts as appropriate.
Suitable contact persons have the technical competence to assess the specific incident and are integrated into the organisation and processes for incident management.
There are increased requirements for the availability of an operator contact person after an IT incident has been reported to the BSI. To ensure smooth incident management in cooperation with the BSI, internal (forwarding) processes should be set up to ensure that appropriate contact persons are alerted after receipt of the information, even outside normal business hours. This applies in particular if you have reported an IT incident to the BSI and expect further queries from the BSI.


