5G Risk Analysis
Several studies on risks and threats in 5G mobile networks were conducted by BSI in cooperation with technical experts in mobile network security as part of the project "5G risk analysis". With these studies, the basis for the definition of critical components and requirements for regulation of 5G/6G networks is expanded and awareness for security in mobile networks is raised
A selection of risk scenarios that affect operators of public and private mobile networks as well as users of mobile networks is used within the risk analysis to determine which subsystems of the 5G network are critical concerning security.
The studies are only available in English language, as the target group is primarily the international IT security community. The studies are also in the context of English publications on this topic.
Framework Document – Methodology, Risk Scenarios and Results
The framework document of the 5G risk analysis contains a summary of the results of all detailed analyses. This shows that all subsystems of a 5G network are critical regarding confidentiality, integrity and availability. The methodology which is based on the threat model PASTA (Process for Attack Simulation and Threat Analysis) and 21 exemplary risk scenarios e.g. failure of emergency calls or eavesdropping of communications are described as well. The relevant subsystems of a 5G network, which are shown in the system diagram, are also briefly presented.
5G Risk Analysis - Framework Document: Methodology, Risk Scenarios and Results
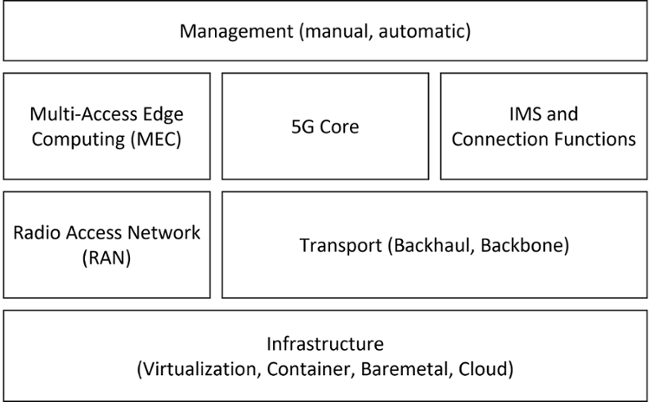
Risk Analysis – 5G Core
The 5G Core is the heart of a 5G network and consists of elementary control functions for control and user plane traffic. In addition to mobility management, the core network is also responsible for authentication of users and accordingly stores sensitive data to identify registered subscribers.
The
5G Risk Analysis - 5G Core Network shows the 5G Core as the central element of a 5G system to be particularly critical regarding security functionalities.
Risk Analysis – 5G Radio Access Network (RAN)
The radio access network (RAN) enables wireless communication within the mobile network. The base stations provide the radio link to the mobile device and usually are connected to the core network via fast optic lines. In 5G networks, distributed base stations are increasingly being used which are connected via logical interfaces.
The
5G Risk Analysis - Detailed Analysis: Radio Access Network (RAN) shows the 5G RAN to be particularly critical regarding the regional availability of mobile communications.
Risk Analysis – Transport Network
In general, data centers and antenna sites in the moblie network are interconnected by wired connections. The transport network is used exclusively for aggregating and transporting data traffic. It contains network equipment for efficient and fast routing to any node in the mobile network.
The
5G Risk Analysis - Detailed Analysis: Transport Network shows the transport infrastructure to be as critical regarding security as the 5G Core.
Risk Analysis – Infrastructure
Modern 5G networks are based on virtualized network functions and therefore require complex infrastructures that enable virtualization and containerization. Additionally, management and orchestration (MANO) of network functions is used. For efficient and automated operation, many logical interfaces are required within the infrastructure subsystem.
The
5G Risk Analysis - Detailed Analysis: Infrastructure shows that the virtualization infrastructure in 5G provides fundamental security functions, but is not as critical as higher-level components in many risk scenarios.
Risk Analysis – IP Multimedia Subsystem (IMS) and Interconnect
The IP multimedia subsystem (IMS) utilizes specific functions and interfaces to enable multimedia services such as telephony or SMS across the different generations of mobile networks. Similarly, roaming networks connect different generations of mobile networks nationally and internationally so that cross-network communication is possible. New components and interfaces in 5G are intended to increase security for the data exchange between networks.
The
5G Risk Analysis - Detailed Analysis: IP Multimedia Subsystem (IMS) and Interconnect Network shows that functions for multimedia services and roaming are very critical in terms of confidentiality, integrity and availability of cross-network data transmission.
Risk Analysis – Multi-Access Edge Computing (MEC)
Relocating computing capacity close to the antenna sites is an efficient way to meet the high performance requirements of modern application scenarios for mobile networks. However, for Multi-access edge computing (MEC), new functions and interfaces are needed that make it possible to operate parts of the 5G Core in distributed data centers or in the public cloud.
The conclusion of the
5G Risk Analysis - Detailed Analysis: Multi-Access Edge Computing (MEC) is that edge computing contains security-critical functions that are currently mainly relevant for use case scenarios in private 5G networks.
Risk Analysis – Management Systems
The configuration of all functionalities and security options of the mobile network is controlled via management systems. These systems can dynamically change all parameters within the various subsystems, either manually or with automated routines. However, no standardized interfaces and functions are usually used, as the configuration of software and hardware is mostly vendorspecific.
The
5G Risk Analysis - Detailed Analysis: Management System shows that management systems can access and influence all subsystems of a 5G network and are therefore particularly critical regarding security of the 5G system.


