Risk levels for vulnerabilities
Within the framework of the CERT Verbund, the foundations for close cooperation between German CERTs have been laid in various projects. The core of an infrastructure for the joint creation and processing of security advisories is the German Advisory Format (DAF), an exchange format for security advisories specially tailored to the needs of the German CERT landscape, which is developed and maintained by CERT-Bund, DFN-CERT, PRESECURE and Siemens-CERT. In it, a classification scheme for vulnerability assessment was agreed upon, which is described in more detail below.
Vulnerability classification scheme
Figure 1 shows the schematic representation of the scheme. A common assessment of the risk of a vulnerability by a group of cooperating CERTs can only be of a general nature, as the local circumstances of the target group will in most cases vary from CERT to CERT. For this reason, a two-step vulnerability assessment process is used in DAF. In the first step, client-specific factors are first factored out. In this phase, a CERT can, for example, adopt an assessment made by another CERT or compare it with its own assessments for quality control purposes. Differences in the assessment of the current damage potential are an indicator that certain facts may have been overlooked or their relevance assessed differently. Only in a second step is the general assessment merged with the client-specific factors in order to facilitate the classification for the recipient of a security message. Information on the status of a vulnerability, type of its exploitation, the damage effect that can be achieved through the exploitation, as well as concrete attack prerequisites serve as the basis for the assessment of vulnerabilities.


Ermittlung des Eintrittspotenzials
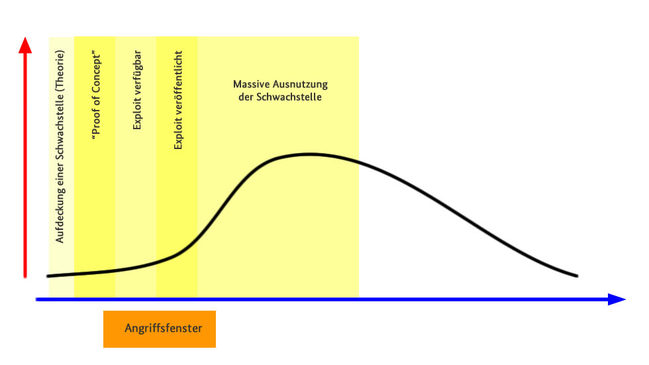
To determine the entry potential, two dimensions are basically included in the assessment: the status of the vulnerability and the type of vulnerability (see Figure 1). The status of a vulnerability goes through a life cycle, the four states of which are described below as examples:
theoretical
In this phase, a (programming) error is discovered, for example, which could possibly lead to a security hole
exploitable
If a proof of concept of a security hole is made, DAF speaks of an exploitable vulnerability.
active
If there are signs that the vulnerability is already being exploited, it is an active vulnerability (for example, an exploit is available).
exploit published
This phase is reached when an attack tool has been published for the vulnerability. We then speak of a vulnerability with a published exploit. Overall, the attack effort decreases.

The exploitation type dimension represents the different ways in which a vulnerability can be exploited. A distinction is made here between manual, automated or self-replicating exploitation. Manual exploitation requires the attacker to perform non-automatable steps to adapt the attack to the circumstances of the attack target. Automated attacks, on the other hand, allow a vulnerability to be exploited at the push of a button, so to speak. Finally, self-replicating attacks can be carried out by worm programs and bots, for example, which take over or use a system after a successful attack to attack other systems.
From the dimensions described above, an entry potential (urgency) can be determined and mapped as follows on a corresponding scale from very low to very high. The following table shows an overview of the various combinations and contains suggestions for determining the urgency or entry potential of a vulnerability.
| Status der Schwachstelle | Verbreitungsmethode | ||
|---|---|---|---|
| manuell | automatisch | replizierend | |
| theoretisch | sehr gering | gering | mittel |
| ausnutzbar | gering | mittel | hoch |
| aktiv | mittel | hoch | hoch |
| Exploit veröffentlicht | mittel | hoch | sehr hoch |
Determining the entry potential
The evaluation of the damage potential is carried out in direct dependence on the impact achieved by exploiting the vulnerability. The necessary attack conditions for a successful exploitation of a vulnerability are considered to be given in this approach (worst case approach). To assess the damage potential, DAF considers which security
objectives can be violated and in which context this can happen. In addition to the security objectives often known from the literature:
Integrity, confidentiality and availability, breaches related to system control (partial or complete control by an attacker) and bypassing security services - e.g. by overriding a firewall - are also considered here. Security breaches can occur in relation to:
- Person (User)
- Service (Application)
- IT-system
- Network
The following table gives an overview of possible combinations and contains a resulting evaluation of the respective damage potential.
| Verlust | Kontext | |||
|---|---|---|---|---|
| Benutzer | Dienst | System | Netzwerk | |
| Übernahme der Kontrolle | hoch | hoch | sehr hoch | sehr hoch |
| Übernahme von Berechtigungen | mittel | mittel | hoch | hoch |
| Integrität | gering | mittel | hoch | hoch |
| Vertraulichkeit | sehr gering | gering | mittel | hoch |
| Verfügbarkeit | sehr gering | gering | mittel | hoch |
| Umgehung von Sicherheitsmaßnahmen | sehr gering | gering | mittel | hoch |
Determination of the current damage potential (risk)
The current damage potential now takes into account, in distinction to
the general damage potential described above, the combination of the
factors "entry potential" and "damage potential" shown in Fig.1.
In our CERT-Bund publications, the client-independent assessment is indicated as "risk level".
| Eintrittspotenzial | Schadenspotential* | ||||
|---|---|---|---|---|---|
| sehr gering | gering | mittel | hoch | sehr hoch | |
| sehr gering | sehr gering | sehr gering | gering | gering | mittel |
| gering | sehr gering | gering | gering | mittel | hoch |
| mittel | gering | gering | mittel | hoch | hoch |
| hoch | gering | mittel | hoch | hoch | sehr hoch |
| sehr hoch | mittel | hoch | hoch | sehr hoch | sehr hoch |
* Risk levels
very low = 1; low =2; medium = 3; high = 4; very high = 5
Determining the clientele-specific risk
If a CERT has detailed information about the local conditions at the recipient of a security message, a target-group-specific assessment of the risk can be made. Taking into account the attack conditions and the IT systems used, the probability of a successful attack at the recipient can be estimated. Together with the metric introduced by DAF -- current damage potential -- the specific risk related to a vulnerability can be derived.


